From apps to infrastructure, internal and external cloud environments are under scrutiny. We explore the top security concerns of cloud users, the challenges enterprises face in resolving vulnerability concerns and a potential solution
by CSO and Ryan English, HP Fortify
 The cloud is now mainstream for the enterprise. An April 2012 IDG Research survey found more than twothirds of respondents—69 percent— reported their companies are consuming or piloting applications or infrastructure via the cloud. This trend is growing. This makes security of data and applications a critical concern. Security vulnerabilities can undermine every advantage the cloud brings. HP Enterprise Security can be a solution to these challenges and make secure applications and a software security culture into business drivers.
The cloud is now mainstream for the enterprise. An April 2012 IDG Research survey found more than twothirds of respondents—69 percent— reported their companies are consuming or piloting applications or infrastructure via the cloud. This trend is growing. This makes security of data and applications a critical concern. Security vulnerabilities can undermine every advantage the cloud brings. HP Enterprise Security can be a solution to these challenges and make secure applications and a software security culture into business drivers.
Challenge
The IDG survey found that fewer than 40 percent of respondents ranked themselves as highly effective in ensuring cloud security. They acknowledge weaknesses in:
- finding and fixing existing application vulnerabilities
- understanding security and risk in the cloud infrastructure
- establishing a productive feedback loop with software developers and vendors
- ability to audit new code and applications for residency in the cloud.
Another self-described weakness is a lack of enterprisewide software security culture. The large majority of application security remains in the hands of IT operations or IT security teams. Only 26 percent report that cloud security is an enterprise-wide effort. But a strong majority -74 percent – know they need to change that. They say creating and sustaining a partnership between IT security and software development and cloud vendors around cloud application security will be a high priority during the next year.
Top concerns
 This desire for change is driven by an increasing awareness of the risks facing enterprises that fail to maintain security. At the top of the list, 89 percent of respondents cite a lack of control over areas where personally identifiable information (PII) is present in the cloud. A loss of PII can be devastating to an enterprise. While the average cost per record breached is estimated to range from $150 to $200, the potential exists for it to be much greater. Also high on the list of concerns, at 76 percent, is cybercrime. The sophistication and ubiquity of cyber attacks means thousands of malware variants can hit major enterprises or cloud providers every day. Numerous surveys have found that corporate data are highly desired by criminals, competitors and nation states.
This desire for change is driven by an increasing awareness of the risks facing enterprises that fail to maintain security. At the top of the list, 89 percent of respondents cite a lack of control over areas where personally identifiable information (PII) is present in the cloud. A loss of PII can be devastating to an enterprise. While the average cost per record breached is estimated to range from $150 to $200, the potential exists for it to be much greater. Also high on the list of concerns, at 76 percent, is cybercrime. The sophistication and ubiquity of cyber attacks means thousands of malware variants can hit major enterprises or cloud providers every day. Numerous surveys have found that corporate data are highly desired by criminals, competitors and nation states.
Benefits
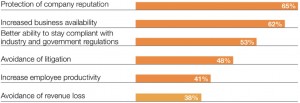
Given the loss of consumer confidence in enterprises that suffer major data breaches, it is not surprising that the most important benefit from good security cited by survey respondents was protection of a company’s reputation. It is not simply the raw cost of lost data that damages an enterprise, although it can be crippling. Significant damage to a brand means lost business in the future from consumers or clients who feel they can no longer trust a vendor. This can be an existential threat. And it is no longer possible to keep major breaches out of the public eye. In late 2011, the SEC issued guidelines that require public companies to disclose security events if they materially affect the entity’s products, services, relationships, or competitive conditions, or if they would make an Sponsored by: investment in the company speculative or risky. Security readiness of applications deployed in the cloud means greater business availability; a notion cited by 62 percent of respondents. The cloud is accessible 24/7, which means customers and clients never have to wait for office hours. Finally, a secure cloud environment allows employees to improve their productivity, through collaboration with colleagues and availability to clients.
Solution
 Effective cloud security must exist in both the internal and external environments. Internally, any vulnerabilities in an enterprise’s software and applications should be resolved before they are deployed to the cloud. The HP Fortify Software Security Center (SSC) is one solution which addresses these internal issues with a suite of integrated solutions for identifying, prioritizing and fixing security vulnerabilities in software, with vulnerability analysis from software development to QA testing – even for applications already deployed.
Effective cloud security must exist in both the internal and external environments. Internally, any vulnerabilities in an enterprise’s software and applications should be resolved before they are deployed to the cloud. The HP Fortify Software Security Center (SSC) is one solution which addresses these internal issues with a suite of integrated solutions for identifying, prioritizing and fixing security vulnerabilities in software, with vulnerability analysis from software development to QA testing – even for applications already deployed.
It is available on-premises or on-demand, and with managed services. This is accomplished by identifying root cause of software security vulnerabilities in both source code (static analysis) and running applications (dynamic analysis). HP Fortify SSC detects more than 470 types of vulnerabilities across 18 development languages and more than 600,000 APIs. It is not enough simply to fix vulnerabilities before deployment. HP Enterprise Security provides a team dedicated to researching application security and emerging threats. It also ensures continuing compliance with industry and government policies and security standards.
On the external level, it is crucial to evaluate an Internet service provider before deploying sensitive company data to the cloud. The cloud can be secure if it is done right, but this requires ‘a huge checklist’ to verify that a vendor is ‘doing what’s needed to be secure’. The verification list includes questions like, “Have they had an application security assessment? Have they had a pen test? What do their policies look like?”. And a lot of times they are not doing it.
