Outlining the growing need for multi-faceted solutions using RFID, when large numbers of people require monitored access into and out of public areas such as retail stores, stadiums and libraries
by Magnus Sundell, Vacon
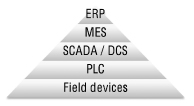
 The Different layers of an industrial automation system are commonly illustrated using the automation pyramid. The top of the pyramid consists of high-level systems such as Enterprise Resource Planning (ERP) solutions, which integrate IT systems across an entire organization. ERPs rely on the services of Manufacturing Execution Systems (MES) for managing individual plants or factories. According to the third layer of the pyramid, a plant is generally operated using Supervisory Control and Data Acquisition (SCADA) or Distributed Control System (DCS), which are industrial control systems used for monitoring and control of processes. Furthermore, SCADA may control and monitor devices such as Programmable Logic Controllers (PLC) or Remote Terminal Units (RTU). In the end, PLCs interact with sensors and actuators on the field device level, performing real-time control as necessary in the process.
The Different layers of an industrial automation system are commonly illustrated using the automation pyramid. The top of the pyramid consists of high-level systems such as Enterprise Resource Planning (ERP) solutions, which integrate IT systems across an entire organization. ERPs rely on the services of Manufacturing Execution Systems (MES) for managing individual plants or factories. According to the third layer of the pyramid, a plant is generally operated using Supervisory Control and Data Acquisition (SCADA) or Distributed Control System (DCS), which are industrial control systems used for monitoring and control of processes. Furthermore, SCADA may control and monitor devices such as Programmable Logic Controllers (PLC) or Remote Terminal Units (RTU). In the end, PLCs interact with sensors and actuators on the field device level, performing real-time control as necessary in the process.
The F-Secure Corporation terminology defines malware as programs and files (e.g. viruses, worms and Trojan horses) which are created and spread in order to cause harm. The term malware is obtained by combining the words ‘malicious’ and ‘software’. Three different types of malware are explained briefly: Worms, Viruses, and Trojan horses. Firstly, worms are self-replicating programs which uses security flaws to spread, often without the user of the machine being aware of this. Worms need not harm the machines, however they quite often consume bandwidth and cause harm due to increased network traffic hindering important information exchange. Worms with payload (i.e. code designed to perform actions on the infected system) can cause damage to the infected machine and its system. Viruses are also designed to self-replicate and spread to new machines. The F-Secure terminology mentions a key characteristic of viruses being the replication mechanism.
The terminology further notes that viruses commonly infect certain files, such as EXE or COM files on PC systems, or the Master Boot Record of hard drives and similar. Trojan horses are, according to the F-Secure terminology a program which appears to perform some action, which may be desired by the user, but in reality performs some other (often undesired) action without the user knowing. Essentially, the function of the program is to make the user allow it inside the safe boundaries of the system, before silently beginning to execute malicious actions.
Malware in industrial automation
For more than 25 years malware has targeted the IT world. Nowadays, malware tries to hide itself as much as possible which makes it difficult to detect. Stuxnet, probably created in 2009, has shown like no other former malware that security issues do not only reside in the regular IT-world, but also in the industrial automation sector. Since general purpose operating systems like Windows are used in the scope of SCADA, vulnerabilities affecting the latter operating systems can also affect the industrial automation sector.
Stuxnet is a worm which is capable of spreading via USB-Sticks from Windows machine to Windows machine. Therefore, an infected machine does not necessarily need to be connected to the Internet. Stuxnet is using zeroday vulnerabilities (vulnerabilities which have not been known) and therefore, it is very difficult to protect against Stuxnet infections even with an up-to-date and patched Windows system. Once Stuxnet has successfully installed itself on a Windows machine, it is capable of searching for automation systems. Moreover, it is looking for Siemens’ Simatic factory systems, the so called SCADA systems. If Stuxnet cannot find any SCADA systems, it will remain silent and does not pursue any activity. On the other hand, if an automation system is found and more specifically high-frequency converter drives, Stuxnet tries to alter its functioning.
The reason why Stuxnet is so special is that it is very complex software and seems to be part of a targeted attack. Simply the size of the binary, 1.5 Mb, is unusually big for malware. Furthermore, it employs 5 exploits, 4 of them being zero-day vulnerabilities. A single zero-day vulnerability costs about $50 000 to $500 000, which makes Stuxnet a very expensive malware. Finally, in order to operate as silently as possible, Stuxnet has been signed with a stolen certificate.
All these three facts already make it clear that this malware has been created by a highly sophisticated attacker with a considerable amount of resources.
 In late 2011 a new malware called Duqu which is very similar to Stuxnet was discovered. Compile times of this new malware could indicate that it has been created in the beginning of 2010. Duqu’s intention is not to alter any functioning of industrial automation systems, but rather to collect sensitive information and send it to a remote server. Therefore, it can be considered more as a kind of Trojan Spy. Although the maturity of malware and the rate of occurrence in the industrial automation sector are still quite low it is foreseeable that attacks may become more frequent and severe in the future. Potential scenarios might include vandalism or sabotaging of industrial plants, municipal services or critical infrastructure just for fun (by everyday hackers) or possibly the hijacking and/or blackmailing of entire plants. In conclusion, there exist highly sophisticated and financially well-established malware creators targeting industrial automation systems. Nevertheless, there are signs that vandalism cases are occurring in the industrial automation sector, with similarities to vandalism caused by hackers in the ICT sector. Therefore it is crucial to analyze the risks and create appropriate defenses.
In late 2011 a new malware called Duqu which is very similar to Stuxnet was discovered. Compile times of this new malware could indicate that it has been created in the beginning of 2010. Duqu’s intention is not to alter any functioning of industrial automation systems, but rather to collect sensitive information and send it to a remote server. Therefore, it can be considered more as a kind of Trojan Spy. Although the maturity of malware and the rate of occurrence in the industrial automation sector are still quite low it is foreseeable that attacks may become more frequent and severe in the future. Potential scenarios might include vandalism or sabotaging of industrial plants, municipal services or critical infrastructure just for fun (by everyday hackers) or possibly the hijacking and/or blackmailing of entire plants. In conclusion, there exist highly sophisticated and financially well-established malware creators targeting industrial automation systems. Nevertheless, there are signs that vandalism cases are occurring in the industrial automation sector, with similarities to vandalism caused by hackers in the ICT sector. Therefore it is crucial to analyze the risks and create appropriate defenses.
Standardization
Generally, standardization aims to provide commonly approved methods and practices to enable transparency in defined areas. With the help of standardization people can do e.g. internet banking safely and securely or use their mobile phones. Also industrial standards facilitate global trade, protect human life (safety) and lately to drive more and more so called ‘green values’. ICT has met the challenges of security for a relatively long period. This can also be seen when standardization activities in security sector are briefly introduced.
ICT security standards
 International telecommunication union (ITU) has group “ITU-T Study Group 17 – Security” which operates and covers a wide spectrum of application areas for security. It has published over seventy standards (ITU-T Recommendations) focusing on security. One key reference is X.509 which has enabled electronic authentication over public networks being an enabler for the rise of e-business. SG 17 is active in standard development and in coordination between applications specific groups (e.g. SmartGrid security) and other organizations. ITU standards are typically an underlying technology in industrial automation security or are linked to industry requirements via other organizations.
International telecommunication union (ITU) has group “ITU-T Study Group 17 – Security” which operates and covers a wide spectrum of application areas for security. It has published over seventy standards (ITU-T Recommendations) focusing on security. One key reference is X.509 which has enabled electronic authentication over public networks being an enabler for the rise of e-business. SG 17 is active in standard development and in coordination between applications specific groups (e.g. SmartGrid security) and other organizations. ITU standards are typically an underlying technology in industrial automation security or are linked to industry requirements via other organizations.
Standardization work in IT security is also done by the International Organization for Standardization (ISO). Committee ISO/IEC JTC 1/SC 6 Telecommunications and Information Exchange Between Systems is developing telecommunication standardization for the exchange of information between open systems. This standardization includes both the lower layers that, as well as the upper layers that support the application protocols and services. Responsible technical committee for the security is JTC 1/SC 27 IT Security techniques.
There are 98 published standards and all of them are ISO/IEC versions. The corresponding technical committee in IEC organization is ISO/IEC JTC 1/SC 27 IT security techniques. The first standard has been published as early as 1998. The focus is on protection of information and ICT. This includes generic methods, techniques and guidelines to address both security and privacy aspects.
Industrial automation standards
Industrial security standardization work under the International Electrotechnical Commission (IEC) is a relatively new area, when compared to IT activities under ISO. Usage of standard IT technologies and open systems in process control has increased the risk of security threats in the industry. Connectivity to business/IT networks is also more and more common today. Also cyber attacks are more and more advanced today. This all means that there is a clear need for industry specific standards/ specifications and references. Technical committee IEC/TC65 [5] and its four sub-committees prepare standards for industrial automation as well as process industry specific standards including security aspects. TC65 has published four generic security standards to this day and there are six standards under construction work.
The focus of these standards is on the network and system level. Preparation of industrial automation security IEC62443-standards is done based on the International Society of Automation (ISA) work. ISA99 committee “Industrial Automation and Control Systems Security” has originally started this activity, which is now utilized by IEC. [6] A brief idea in this standardization is to divide process or plant in security zones connected by conduits and determine security by security assurance levels (SAL’s) (alike with safety integrity levels in functional safety). Detailed definition work based on this approach for the security system is ongoing.
Power systems
The availability of electric power systems is vital for today’s infrastructure and as control of these systems is based on digital communications today and they are geographically wide systems, the security challenge is addressed with industry specific standard. Communications protocols for substation automation like IEC 61850 are included. ISO/IEC joint technical committee JTC 1 SC37 is preparing standardization of generic biometric technologies pertaining to human beings to support interoperability and data interchange among applications and systems.
Standardization and related activities has strong position in ICT security. Nature of standardization fits well in security as it offers transparent and open platform for development. Technical solutions are reviewed by experts globally and the results are available in the public domain for use in industry. Security of automation is newer topic. However, there has been active work by society and wider IEC standardization is ongoing. Industry should adopt present automation security standardization and prepare for the forthcoming outcome. There are proven security methods available; it is more an industry task to apply them in proper and relevant extent. Some limitations will apply in security realization due to historical reasons, but the current IEC standardization approach gives a good starting point towards better automation security.
Security programs
 Security in industrial automation has got much more attention after the Stuxnet case. Measures to improve and implement security have been started before Stuxnet, but thoughts and attitudes have now changed. Traditional fieldbuses are missing security aspects in many ways. There are no standardized rules and requirements for field devices against security threats like tampering, hacking and similar activities. This means that it will be difficult to implement security measures in lower automation levels by retrofitting or reengineering current communication standards in the short term. Therefore, it is essential that end-users and owners/operators apply feasible cyber security programs in their processes and plants to get protection against attacks via upper automation levels and to restrict physical access in affected zones. Existing practices of ICT business and already published industrial standards and guidelines can be used as a foundation for this work.
Security in industrial automation has got much more attention after the Stuxnet case. Measures to improve and implement security have been started before Stuxnet, but thoughts and attitudes have now changed. Traditional fieldbuses are missing security aspects in many ways. There are no standardized rules and requirements for field devices against security threats like tampering, hacking and similar activities. This means that it will be difficult to implement security measures in lower automation levels by retrofitting or reengineering current communication standards in the short term. Therefore, it is essential that end-users and owners/operators apply feasible cyber security programs in their processes and plants to get protection against attacks via upper automation levels and to restrict physical access in affected zones. Existing practices of ICT business and already published industrial standards and guidelines can be used as a foundation for this work.
 A security program shall be a de facto – requirement for new installations and plants. Risks shall be identified and preventive measures shall be applied through the delivery chain from customer requirements to system integrators and device vendors. Also installation, commissioning, maintenance, service and operator staff needs to follow proper procedures in order to ensure that the security of customer operations is not at risk. Field level communication developers and field devices manufacturers need to place more focus on security in future development. There are easier and more difficult areas to handle, but as this Pandora’s box is once opened there is no turning back. Transparent and quantitative methods are required and on-going standardization work needs strong support from all sides.
A security program shall be a de facto – requirement for new installations and plants. Risks shall be identified and preventive measures shall be applied through the delivery chain from customer requirements to system integrators and device vendors. Also installation, commissioning, maintenance, service and operator staff needs to follow proper procedures in order to ensure that the security of customer operations is not at risk. Field level communication developers and field devices manufacturers need to place more focus on security in future development. There are easier and more difficult areas to handle, but as this Pandora’s box is once opened there is no turning back. Transparent and quantitative methods are required and on-going standardization work needs strong support from all sides.
The automation business has creditable history solving challenges e.g. in safety, EMC and functional safety – it is time for security now. An extract from Vacon’s White Paper: Industrial Automation Security on Fieldbus and Field Device Level.
