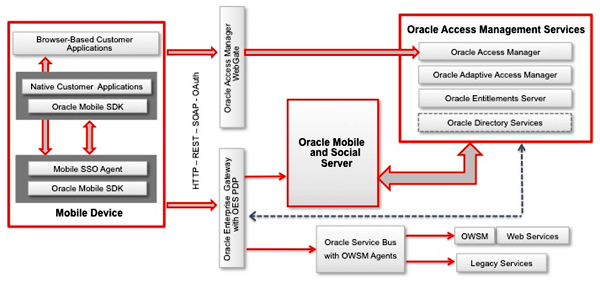
How a system with a server that interfaces with existing backend infrastructures, acts as an intermediary for mobile client applications and backend ID services
by Marc Chanliau, Oracle
 Mobile computing gradually allows us to make the elusive ‘anytime, anywhere access’ mantra a reality. Online social identities allow us to access web sites using existing identities from leading social networks such as Facebook, LinkedIn, or Twitter. Mobile computing is blurring the difference between personal and business use. Many companies recognize the importance of personal mobile devices for business use: users can access corporate resources from their mobile devices at their convenience to improve productivity, and companies can enable access to corporate resources through native mobile applications to improve user experience. However, introducing mobile devices in the enterprise presents additional security challenges.
Mobile computing gradually allows us to make the elusive ‘anytime, anywhere access’ mantra a reality. Online social identities allow us to access web sites using existing identities from leading social networks such as Facebook, LinkedIn, or Twitter. Mobile computing is blurring the difference between personal and business use. Many companies recognize the importance of personal mobile devices for business use: users can access corporate resources from their mobile devices at their convenience to improve productivity, and companies can enable access to corporate resources through native mobile applications to improve user experience. However, introducing mobile devices in the enterprise presents additional security challenges.
Mobile devices need to blend seamlessly into the corporate computing landscape in order to preserve security without disrupting the workflow of the enterprise. Typically, applications running natively on mobile devices need to integrate with the enterprise-wide identity governance and access control infrastructure for security and compliance reasons. Oracle’s Mobile and Social Access Management is a single, integrated solution addressing both mobile computing and social networks security requirements in order to allow organizations to fully benefit from these disruptive technologies without risk. The solution includes a new component, the Oracle Mobile and Social server, designed to secure mobile applications leveraging the enterprise’s existing back-end identity management infrastructure in terms of single sign-on between browser-based and native mobile applications, strong authentication, device fingerprinting, and device-context-based authorization. This service also provides client software to weave security into native mobile applications for tight integration with identity management. In addition, it enables enterprises to securely leverage social identities for personalization and federated sign-on .
Social access
Mobile computing provides new opportunities for accessing corporate resources, but existing infrastructures limit remote or mobile access to browser-based functionality. Mobile users need broader access to more applications and data, from any wireless device. However, accessing corporate resources from and storing data on devices that are often owned by their users presents security challenges to the enterprise.
Indeed, a smart phone can easily be lost or stolen, with important data exposed to non-authorized parties. With more and more organizations establishing a presence on social networks, IT departments require support for social identities, which rely on lighter weight security standards than enterprise identities but are better adapted to the requirements of social networks.
For example, some websites may require users to provide access tokens obtained from Facebook or Google in order to be authenticated to their services. Oracle’s server interfaces with existing backend identity management infrastructures, acting as an intermediary between supported mobile client applications and backend identity services. This approach decouples the client applications from the backend infrastructure so that a backend infrastructure can be modified without having to update mobile client programs.
Enterprise security
By extending the unique identity and access management platform approach, customers can securely bring advanced mobile computing into the enterprise. In a typical reference architecture (as shown in Figure 2), the Mobile and Social service leverages multiple components of the identity and access management.
Authenticating users
The mobile and social solution provides authentication services that let you extend an existing authentication infrastructure to new mobile applications as well as non-mobile applications already in place (authentication is provided by OAM and OAAM when strong authentication is required). Mobile services support the following common token types: a user token granting the token bearer with the permissions associated with the person who has been authenticated; an access token granting access to a specific protected resource, such as an enterprise web application; a client token granting access to a non-mobile device, such as a web application or server application.
Mobile services also use client registration handles, which are similar to client tokens. A client registration handle represents a mobile client application running on a mobile device, such as one running Apple iOS or Android. Because mobile devices and non-mobile devices present different security challenges, mobile authentication and non-mobile authentication are managed separately by the service. Mobile services and social ID services can be configured to work together. For example, social ID services can be used to let users authenticate with Google, Facebook, or Twitter, and mobile services to provide local authentication functionality, or generate a user token by accepting a user identity assertion from a social identity provider.